We will begin the implementation of an authorization server with minimal api using OpenIddict, initially with its minimum features.
OpenIddict is a stack that provides features for supporting OAuth2 and OIDC in applications. By adding the NuGet package references of OpenIddict to the project, we ensure the standards that must be followed to implement an authorization server.
We will build the authorization server from an ASP.NET Core project using minimal API on the authentication endpoints.
Minimum requirements
To quickly implement a server with the minimum requirements, we should first install the following OpenIddict NuGet packages that add server functionalities to the project:
OpenIddict.Core OpenIddict.Server.AspNetCoreNext, we configure OpenIddict by creating an extension that will be added to the application pipeline. So, we create a folder called Extensions at the root of the project, where all the application extensions will be stored. Inside this folder, we create the following OpenIddictExtensions class:
namespace AuthorizationServer.Extensions; public static class OpenIddictExtensions { public static WebApplicationBuilder AddOpenIddict(this WebApplicationBuilder builder) { builder.Services .AddOpenIddict() .AddServer(options => { options.AllowClientCredentialsFlow(); options.SetTokenEndpointUris("connect/token"); options.AddDevelopmentEncryptionCertificate() .AddDevelopmentSigningCertificate(); options.DisableAccessTokenEncryption(); options.UseAspNetCore() .EnableTokenEndpointPassthrough(); }); return builder; } }The AddOpenIddict extension registers the OpenIddict services.
The AddServer extension registers the token server services, which must include the definition of the following configurations: AllowClientCredentialsFlow to enable support for the client credentials authorization flow; SetTokenEndpointsUris to define the relative or absolute URIs associated to the token endpoint; encryption and signing certificates, where we use AddDevelopmentEncryptionCertificate and AddDevelopmentSigningCertificate to generate certificates in a development environment; UseAspNetCore to register the OpenIddict server services for ASP.NET Core. Additionally, we can optionally define the following configurations: DisableAccessTokenEncryption to disable encryption of the JWT access token; EnableTokenEndpointPassthrough to enable initial handling of OpenID Connect requests by OpenIddict on endpoints that must be created with the same route as the authentication endpoint been deployed.
Let’s take the opportunity to organize and remove code that will not be used in Program.cs:
using AuthorizationServer.Endpoints; using AuthorizationServer.Extensions; var builder = WebApplication.CreateBuilder(args); { builder.AddOpenIddict(); builder.Services.AddEndpointsApiExplorer(); builder.Services.AddSwaggerGen(); } var app = builder.Build(); { if (app.Environment.IsDevelopment()) { app.UseSwagger(); app.UseSwaggerUI(); } app.UseHttpsRedirection(); app.Run(); }Running the server
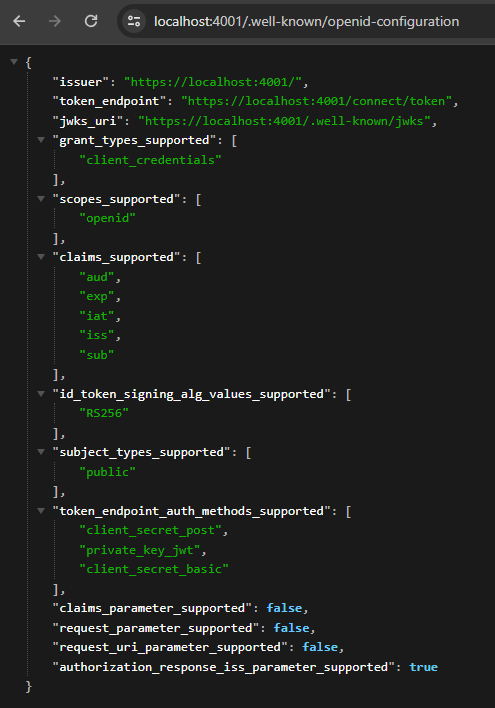
After implementing the minimum requirements, the server integrates a discovery mechanism defined by OpenID Connect, called OpenID Connect Discovery, where OpenID server resources metadata is published at a well-known url.
The authorization server is already available, although it is not yet functional. We can verify this by running the server at the OpenID Connect Discovery URL, which is:
https://localhost:4001/.well-known/openid-configurationSo, the server metadata will be displayed: